DARTS Connectivity (Crime -> SDS)
Network Flow
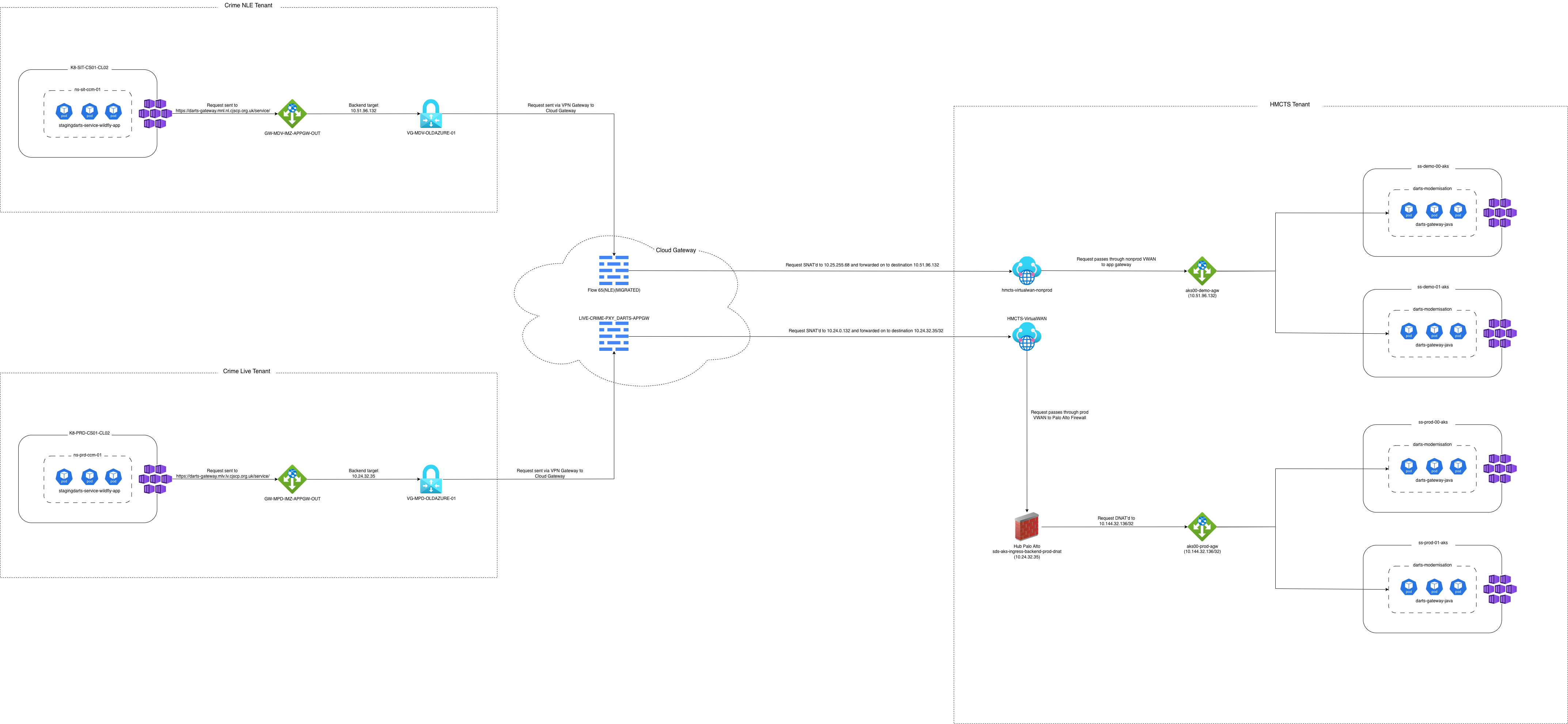
Above is a network flow diagram outlining the connectivity between DARTS in Crime and DARTS in SDS.
In summary:
- Request sent from stagingdarts pod to outbound App Gateway.
- App Gateway forwards traffic via VPN Gateway to Cloud Gateway network.
- Request is SNATd by appropriate Cloud Gateway firewall rule and sent onward to VWAN within HMCTS tenant.
- Request is forwarded to the appropriate AKS App Gateway via the Palo Alto Firewall.
- AKS App Gateway sends request on to a darts-gateway pod on one of the AKS clusters in its backend pool.
Outbound Application Gateway Configuration
There is an outbound App Gateway in each of the Crime tenants:
The gateways have listeners which listen for requests sent to either of these two hostnames:
- https://darts-gateway.mnl.nl.cjscp.org.uk (NonLive)
- https://darts-gateway.mlv.lv.cjscp.org.uk (Live)
When a request is received, it is forwarded on to the specified backend target. In NonLive the target is the SDS Demo AKS backend App Gateway(aks00-demo-agw) via Palo Alto ingress(sds-aks-ingress-backend-demo), and in Live the target is the SDS Prod AKS backend App Gateway(aks00-demo-agw) via Palo Alto DNAT ingress(sds-aks-ingress-backend-prod-dnat).
Cookie-based affinity is enabled on both gateways for sticky sessions.
Outbound requests will have the hostname overridden and set to the corresponding SDS DARTS Gateway for that environment:
- http://darts-gateway.demo.platform.hmcts.net (NonLive)
- http://darts-gateway.platform.hmcts.net (Live)
TLS Certificates
Both DARTS listeners have TLS certificates associated. The certs were generated in Hashicorp Vault and are imported into Azure Key Vault via automation in cpp-aks-ops. Auto-renewal is also configured in this repo so there should be no need for manual intervention.
Relevant Repositories
- cpp-terraform-azurerm-imz - Terraform code for Application Gateways.
- cpp-terraform-network - Terraform code for Private DNS config.
- cpp-aks-ops - Listener TLS certificate automation.
Dynatrace Monitoring
Monitoring has been configured within Dynatrace to trigger alerts when the backend pool of the outbound App Gateway becomes unhealthy.
- Crime - DARTS - PROD - Strategic Platform - Live - Dynatrace Connection
- DARTS - Azure Application Gateway unhealthy hosts - DARTS Metric Event