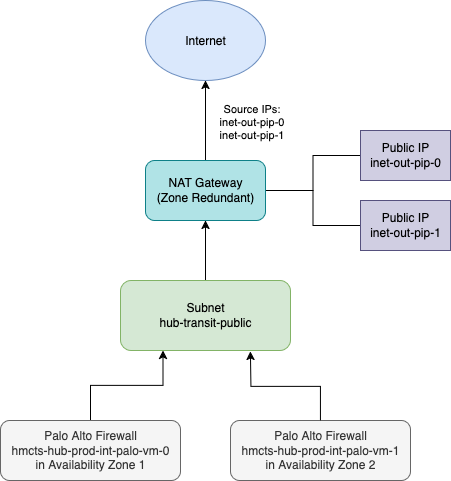
NAT Gateway - Egress Traffic Flow
Overview
The NAT Gateway is a managed Azure service that provides outbound internet connectivity for resources in our virtual networks. It has been implemented to centralize and improve the management of egress traffic that was previously handled directly by our Palo Alto firewall VMs.
Architecture
- NAT Gateway deployed with zone redundancy for high availability
- Public IP addresses attached to the NAT Gateway
- Palo Alto firewalls route traffic through the NAT Gateway for internet egress
- Centralized outbound connectivity management
Configuration Details
Public IP Addresses
The NAT Gateway is configured with the following public IP addresses (Production environment):
hmcts-hub-prod-int-palo-inet-out-pip-0hmcts-hub-prod-int-palo-inet-out-pip-1
These IPs were previously assigned to the individual Palo Alto firewall VMs.
Routing Configuration
- Subnet:
hub-transit-publicsubnet routes traffic through the NAT Gateway - Firewall Integration: Palo Alto firewalls maintain their security inspection role while delegating NAT functions to the gateway
- Availability Zones: NAT Gateway provides zone-redundant connectivity
Monitoring and Troubleshooting
Azure Portal Access
| Environment | Instance |
|---|---|
| Sandbox | hmcts-hub-sbox-int-nat-gateway |
| Non-Prod | hmcts-hub-nonprodi-nat-gateway |
| Production | hmcts-hub-prod-int-nat-gateway |
Key Metrics to Monitor
- SNAT Connection Count: Monitor active outbound connections
- SNAT Port Utilization: Track port usage to prevent exhaustion
- Data Processed: Monitor bandwidth utilization
- Packet Drop Count: Identify potential connectivity issues
Related Documentation
This page was last reviewed on 11 July 2025.
It needs to be reviewed again on 11 July 2026
by the page owner platops-build-notices
.
This page was set to be reviewed before 11 July 2026
by the page owner platops-build-notices.
This might mean the content is out of date.