TLS certificates
Where technically suitable, all new HMCTS domains must use automated certificate techniques and services, such as Microsoft managed certificates (most preferred) or LetsEncrypt (uses ACME).
Over time, existing HMCTS domains must also be considered for migration to automated certificate provisioning and management techniques (preferably on their next certificate renewal cycle in advance of expiry) in order to reduce the consequences and management overheads of manual certificate renewal.
HMCTS acknowledges that not all systems support automated certificate management, but leveraging such technology where possible reduces management overheads, the costs of such overheads and the consequences of unexpected certificate expiry.
If your site is being hosted on:
Then you must use Microsoft managed certificates
You can automatically generate/deploy an Azure-manged certificate by copying an existing site in Azure Platform Terraform
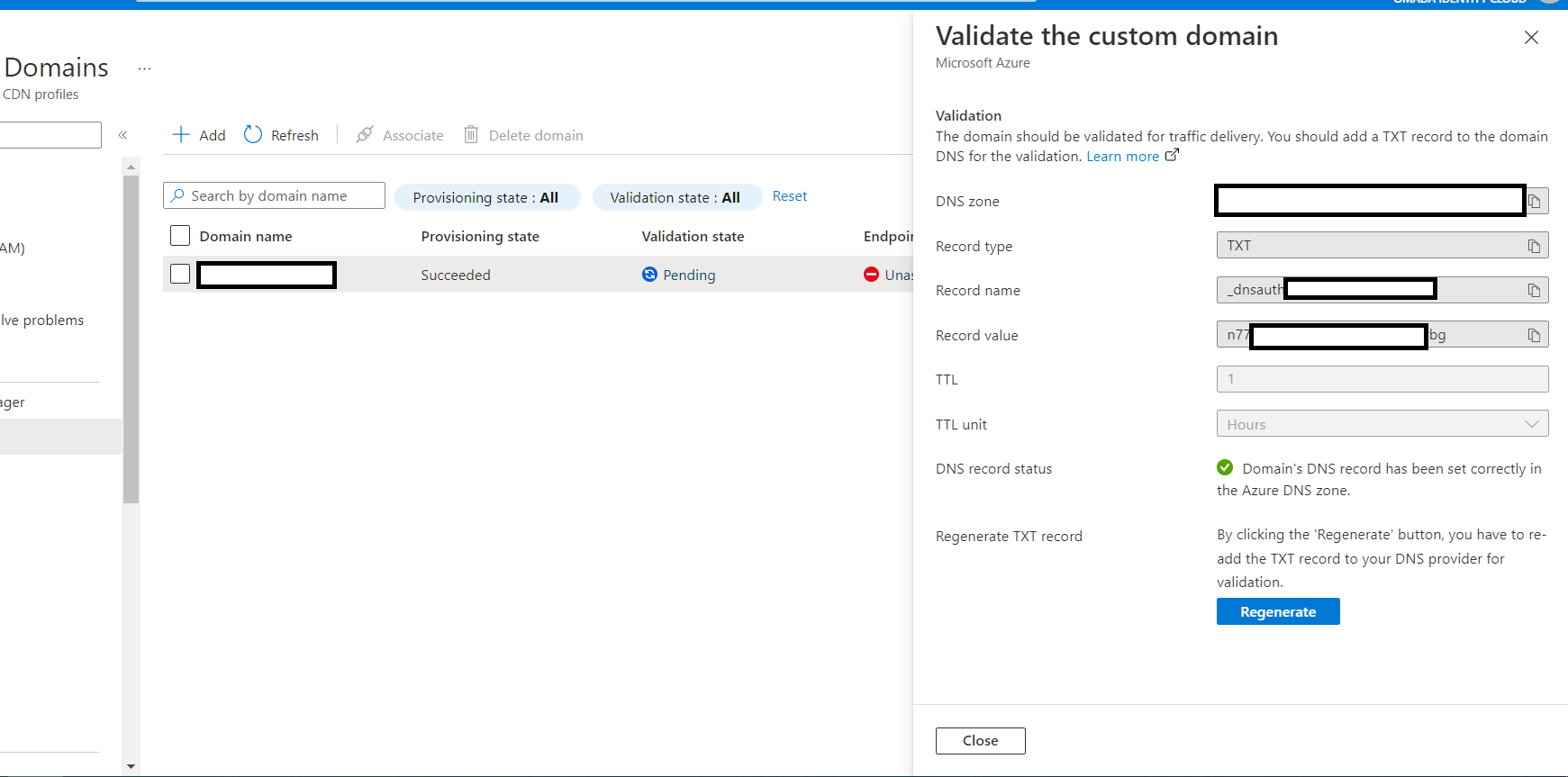
Please note, if the certificate status on ‘domains’ under Frontdoor in Azure portal does not show as ‘deployed’, you will need to manually validate the certificate by creating a TXT record on Azure-public-DNS like in this example PR
You can view the TXT record that needs created by clicking on the status under ‘validation state’
Manual certificate requests
If you cannot use a managed certificate then please raise a request in #platops-help, the ticket should contain the following information:
- Where the certificate is to be hosted
- DNS Name and SANS
ACME Certificates
Let’s Encrypt is a free, automated and open CA. ACME protocol is used to automate the certificate issuance. We are using Key Vault Acmebot function app as an ACME client.
Key Vault Acmebot is deployed from this repository azure-enterprise-acme via this azure-devops pipeline, there is one instance per subscription.
The naming convention for keyvaults and function App are acme<subscription name without hyphens>, sharedservices is replaced with sds because of length limits. e.g. acmedtssdstest.
The naming convention for certificate name in Key Vault is <DNS Name/wildcard>-<DNSZone> separated by hyphen. E.g. hmi-apim-test-platform-hmcts-net, wildcard-test-platform-hmcts-net.
You may need to use ACME certificate due to managed certificate limitations in Front Door by updating the ssl_mode and custom_domain attributes in the Front Door config, here is an example in azure-platform-terraform.
see Create Certificates to create and renew certificates.