Managing Manual Key Vault Secrets
Some secrets cannot be automated via Terraform and therefore we need to add them manually to the Key Vaults.
Please note that we would advise to always go down the Terraform route where possible.
Manual Secrets
The easiest option is to add the secrets manually directly to the project Key Vault. Using the CNP-Module-Key-Vault will grant the Developers group the correct permissions to enable you to add these.
We would also advise to tag your secrets to easily identify between Terraform and manually created secrets.
Secret Store
You can create a secret store much like how Azure DevOps has a Library for secure values.
The concept here is a separate Key Vault for your manually created secrets and then your project Key Vault which will only contain secrets created by Terraform.
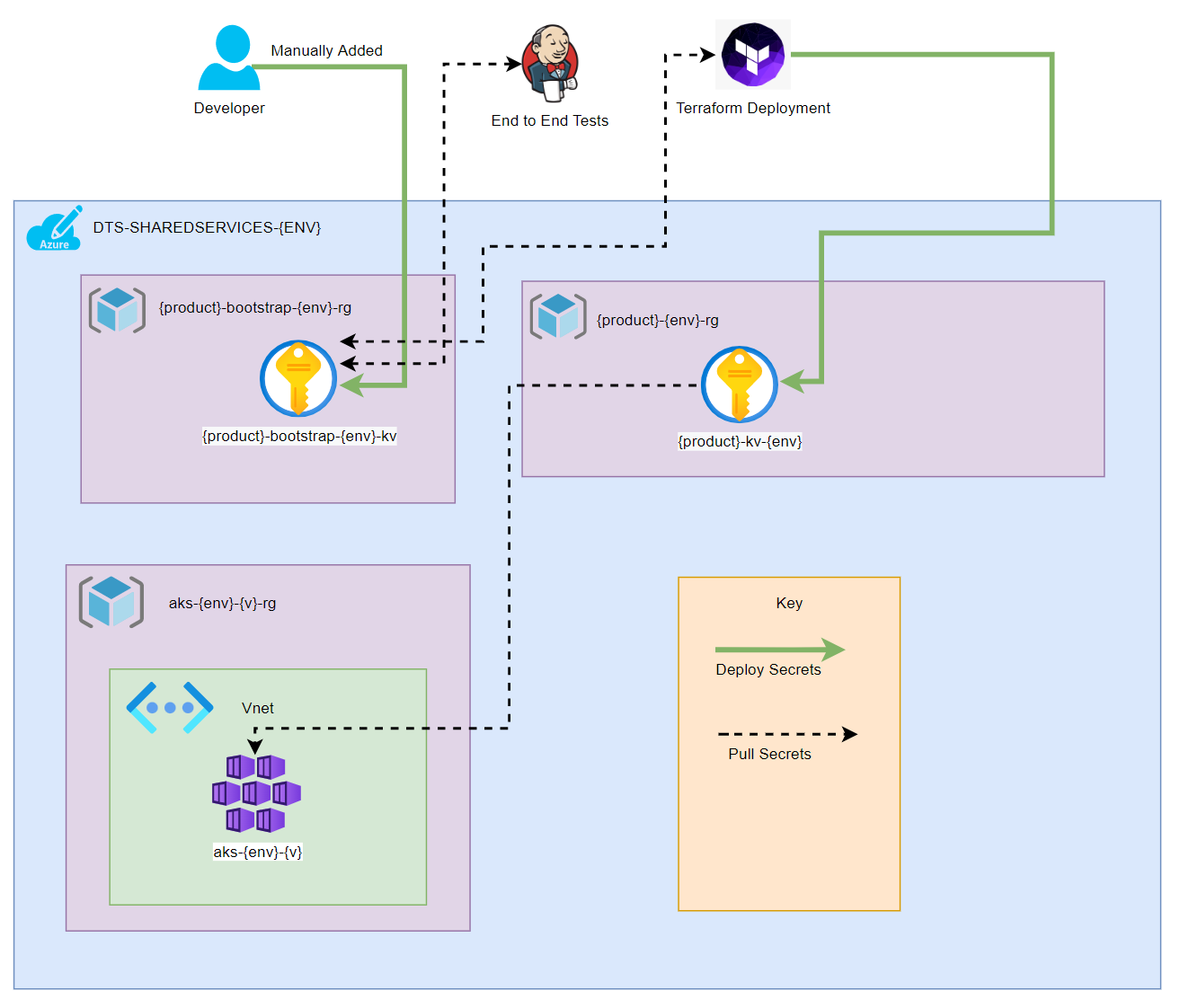
Setup Secret Store
Start by creating your Secret Store Key Vault Repositories following Create a Github Repository. You can then add your Key Vault using the CNP-Module-Key-Vault for example PIP-Shared-Infrastructure-Bootstrap
Import Secrets to Project Key Vault
Now in your project Key Vault you can use the below example to import named secrets. These can be generic secrets shared between environments, or you can add environment specific secrets.
This can also be use for certficates as per this example PIP tf-kv-certs-bootstrap
locals {
secret_store_secrets = ["example-secret", "environment-specific-secret-${var.env}"]
}
data "azurerm_key_vault" "secret_store" {
name = "${var.product}-store-kv-${var.env}"
resource_group_name = "${var.product}-store-${var.env}-rg"
}
data "azurerm_key_vault_secret" "secret_store" {
for_each = { for secret in local.secret_store : secret => secret }
name = each.value
key_vault_id = data.azurerm_key_vault.secret_store.id
}
resource "azurerm_key_vault_secret" "secret_store" {
for_each = data.azurerm_key_vault_secret.secret_store
key_vault_id = module.this.key_vault_id
name = each.value.name
value = each.value.value
tags = merge(var.tags, {
"source" : "secret store ${data.azurerm_key_vault.bootstrap_kv.name} secrets"
})
content_type = "Manual Secret"
}
You can also access these via Jenkins for Smoke and Functional Tests following the guide on cnp-jenkins-library